一、Java层分析

二、Native层分析
1、Java_cn_pojie52_cm01_MainActivity_check
首先分析入参出参和大体流程。


2、sub_B90
接下来看下sub_B90。
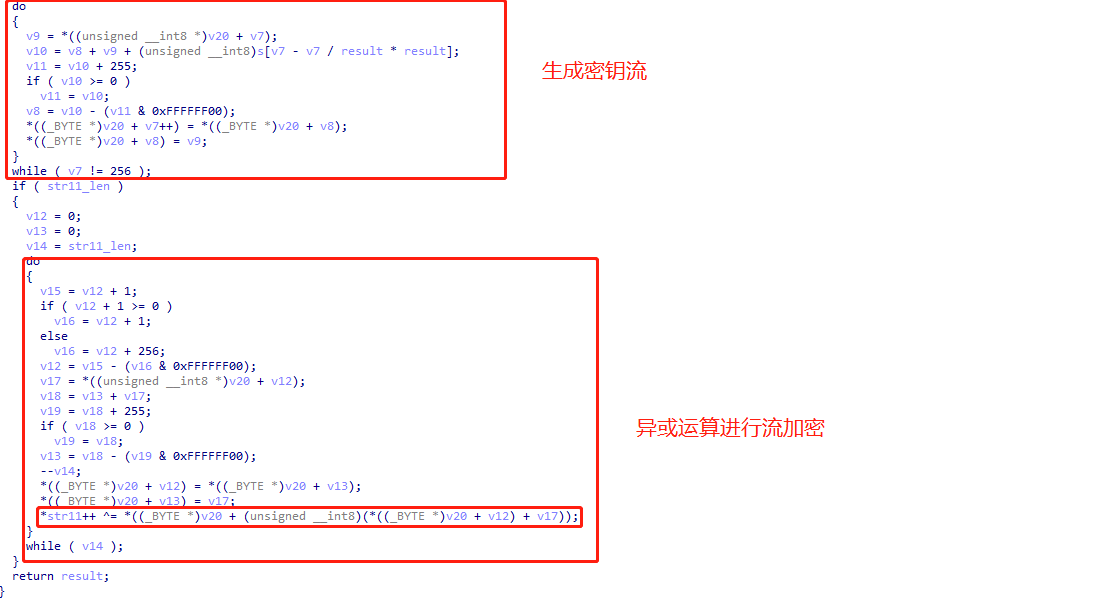
 其中主要部分进行了两次循环,第一个大循环到256次,第二个里面有异或运算,这两个特征一出我们大概率可以确定是RC4。
其中主要部分进行了两次循环,第一个大循环到256次,第二个里面有异或运算,这两个特征一出我们大概率可以确定是RC4。
 使用frida hook一下,看下出入参。
使用frida hook一下,看下出入参。
function hook_sub_B90(){
var offset = 0x0B90;
var base_model = Process.getModuleByName("libnative-lib.so")
var sub_b90_address = base_model.base.add(offset);
console.log("hook_sub_B90");
var temp_address = 0x0;
Interceptor.attach(sub_b90_address,{
onEnter:function(args){
console.log("----------hook_sub_B90----------")
console.log("onEnter")
temp_address = args[0];
console.log(hexdump(args[0]));
console.log(args[1]);
console.log(hexdump(args[2]));
},
onLeave:function(retval){
console.log("onLeave")
console.log(hexdump(temp_address))
console.log("----------end----------")
}
})
}
----------hook_sub_B90----------
onEnter
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
7ffb123178 61 61 61 61 61 73 73 73 73 73 64 64 64 64 64 66 aaaaasssssdddddf
7ffb123188 66 66 66 66 67 67 67 67 67 68 68 68 68 68 00 00 ffffggggghhhhh..
7ffb123198 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb1231a8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb1231b8 71 33 8c d6 18 84 ee 38 50 34 12 fb 7f 00 00 00 q3.....8P4......
7ffb1231c8 00 5c f1 7c 7a 00 00 00 fc 77 65 eb 79 00 00 00 .\.|z....we.y...
7ffb1231d8 00 5c f1 7c 7a 00 00 00 d0 32 12 fb 7f 00 00 00 .\.|z....2......
7ffb1231e8 ac 30 ef 8b 79 00 00 00 a8 a1 19 ec 79 00 00 00 .0..y.......y...
7ffb1231f8 18 41 12 fb 7f 00 00 00 02 00 00 00 b8 ca f0 15 .A..............
7ffb123208 18 1f f5 15 07 00 00 00 6e da 59 f6 79 00 00 00 ........n.Y.y...
7ffb123218 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123228 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123238 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123248 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123258 00 00 00 00 00 00 00 00 00 5c f1 7c 7a 00 00 00 .........\.|z...
7ffb123268 00 00 00 00 00 00 00 00 00 5c f1 7c 7a 00 00 00 .........\.|z...
0x1e
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
79eb658190 61 72 65 79 6f 75 73 75 72 65 3f 3f 3f 3f 3f 3f areyousure??????
79eb6581a0 00 2a 13 3f 28 2d 34 92 9d bb 36 92 92 cd 48 b7 .*.?(-4...6...H.
79eb6581b0 13 39 cb c9 c7 a9 4c cb 46 43 4d 24 da 50 d9 4c .9....L.FCM$.P.L
79eb6581c0 4f 0b 0d 05 0a 13 07 81 21 a0 00 00 00 00 00 00 O.......!.......
79eb6581d0 00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f ................
79eb6581e0 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f ................
79eb6581f0 20 21 22 23 24 25 26 27 28 29 2a 2b 2c 2d 2e 2f !"#$%&'()*+,-./
79eb658200 30 31 32 33 34 35 36 37 38 39 3a 3b 3c 3d 3e 3f 0123456789:;<=>?
79eb658210 40 41 42 43 44 45 46 47 48 49 4a 4b 4c 4d 4e 4f @ABCDEFGHIJKLMNO
79eb658220 50 51 52 53 54 55 56 57 58 59 5a 5b 5c 5d 5e 5f PQRSTUVWXYZ[\]^_
79eb658230 60 61 62 63 64 65 66 67 68 69 6a 6b 6c 6d 6e 6f `abcdefghijklmno
79eb658240 70 71 72 73 74 75 76 77 78 79 7a 7b 7c 7d 7e 7f pqrstuvwxyz{|}~.
79eb658250 80 81 82 83 84 85 86 87 88 89 8a 8b 8c 8d 8e 8f ................
79eb658260 90 91 92 93 94 95 96 97 98 99 9a 9b 9c 9d 9e 9f ................
79eb658270 a0 a1 a2 a3 a4 a5 a6 a7 a8 a9 aa ab ac ad ae af ................
79eb658280 b0 b1 b2 b3 b4 b5 b6 b7 b8 b9 ba bb bc bd be bf ................
onLeave
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
7ffb123178 b0 3b 67 f1 25 95 b4 96 ad 5b 93 96 02 f5 ac e3 .;g.%....[......
7ffb123188 24 b9 9f 86 e5 66 4c 5c 5f 0b 5f d5 46 25 00 00 $....fL\_._.F%..
7ffb123198 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb1231a8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb1231b8 71 33 8c d6 18 84 ee 38 50 34 12 fb 7f 00 00 00 q3.....8P4......
7ffb1231c8 00 5c f1 7c 7a 00 00 00 fc 77 65 eb 79 00 00 00 .\.|z....we.y...
7ffb1231d8 00 5c f1 7c 7a 00 00 00 d0 32 12 fb 7f 00 00 00 .\.|z....2......
7ffb1231e8 ac 30 ef 8b 79 00 00 00 a8 a1 19 ec 79 00 00 00 .0..y.......y...
7ffb1231f8 18 41 12 fb 7f 00 00 00 02 00 00 00 b8 ca f0 15 .A..............
7ffb123208 18 1f f5 15 07 00 00 00 6e da 59 f6 79 00 00 00 ........n.Y.y...
7ffb123218 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123228 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123238 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123248 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ffb123258 00 00 00 00 00 00 00 00 00 5c f1 7c 7a 00 00 00 .........\.|z...
7ffb123268 00 00 00 00 00 00 00 00 00 5c f1 7c 7a 00 00 00 .........\.|z...
----------end----------
3、sub_D90
接下来分析sub_D90,函数逻辑比较复杂就不先细分析,先上Hook,返回值v9会和v19做比较,既然这个部分在RC4异或处理后,那我们大胆猜测是base64(当然只是进行了某种假想并没有进行验证,有可能猜错,但是不影响分析)。
[Pixel 2 XL::cn.pojie52.cm01]-> ----------hook_sub_d90----------
onEnter
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
7ff85f3278 b0 3b 67 f1 25 95 b4 96 ad 5b 93 96 02 f5 ac e3 .;g.%....[......
7ff85f3288 24 b9 9f 86 e5 66 4c 5c 5f 0b 5f d5 46 25 00 00 $....fL\_._.F%..
7ff85f3298 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f32a8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f32b8 35 cc 85 e5 c3 15 12 01 50 35 5f f8 7f 00 00 00 5.......P5_.....
7ff85f32c8 00 7c 5c fc 72 00 00 00 90 34 34 77 72 00 00 00 .|\.r....44wr...
7ff85f32d8 00 7c 5c fc 72 00 00 00 d0 33 5f f8 7f 00 00 00 .|\.r....3_.....
7ff85f32e8 ac 30 53 0b 72 00 00 00 a8 91 90 6b 72 00 00 00 .0S.r......kr...
7ff85f32f8 18 42 5f f8 7f 00 00 00 02 00 00 00 b0 ed 55 13 .B_...........U.
7ff85f3308 38 bd c8 12 07 00 00 00 6e 2a c0 75 72 00 00 00 8.......n*.ur...
7ff85f3318 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f3328 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f3338 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f3348 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
7ff85f3358 00 00 00 00 00 00 00 00 00 7c 5c fc 72 00 00 00 .........|\.r...
7ff85f3368 00 00 00 00 00 00 00 00 00 7c 5c fc 72 00 00 00 .........|\.r...
0x1e
onLeave
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
72fc650930 73 44 74 6e 38 53 57 56 74 4a 61 74 57 35 4f 57 sDtn8SWVtJatW5OW
72fc650940 41 76 57 73 34 79 53 35 6e 34 62 6c 5a 6b 78 63 AvWs4yS5n4blZkxc
72fc650950 58 77 74 66 31 55 59 6c 00 00 00 00 00 00 00 00 Xwtf1UYl........
72fc650960 4a 61 76 61 5f 63 6e 5f 70 6f 6a 69 65 35 32 5f Java_cn_pojie52_
72fc650970 63 6d 30 31 5f 4d 61 69 6e 41 63 74 69 76 69 74 cm01_MainActivit
72fc650980 79 5f 63 68 65 63 6b 00 68 b6 92 6f 72 00 00 00 y_check.h..or...
72fc650990 c0 50 99 6a 72 00 00 00 c0 09 65 fc 72 00 00 00 .P.jr.....e.r...
72fc6509a0 f0 09 65 fc 72 00 00 00 01 c0 d4 70 00 00 00 00 ..e.r......p....
72fc6509b0 40 f9 62 fc 72 00 00 00 00 70 f4 6b 72 00 00 00 @.b.r....p.kr...
72fc6509c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
72fc6509d0 90 09 65 fc 72 00 00 00 01 e0 f3 6f 00 00 00 00 ..e.r......o....
72fc6509e0 c0 fa 62 fc 72 00 00 00 01 70 f4 6b 72 00 00 00 ..b.r....p.kr...
72fc6509f0 90 09 65 fc 72 00 00 00 b0 0a 65 fc 72 00 00 00 ..e.r.....e.r...
72fc650a00 20 eb 61 fc 72 00 00 00 01 e0 f3 6f 00 00 00 00 .a.r......o....
72fc650a10 80 fb 62 fc 72 00 00 00 01 70 f4 6b 72 00 00 00 ..b.r....p.kr...
72fc650a20 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
----------end----------
暂时不看sub_D90里面的逻辑,先根据猜测的来,那么整体逻辑大概如下。

在之前我们了解到,RC4是对称加密算法,就是说在进行流式加密/解密时,用的是相同的秘钥进行的异或运算,那么我们是否可以根据运算后的flag,去跟秘钥做一次异或运算,获得我们应该输入的字符串那?答案是:okkk!
4、获取v19
首先我们要找到v19的值,v19在比较的时候已经组装完毕了,所以我们要在此处hook,拿出v19的值。
看下汇编指令,v19的值在X9临时寄存器里面,只有hook 0xB30的位置就能取出X9的值。

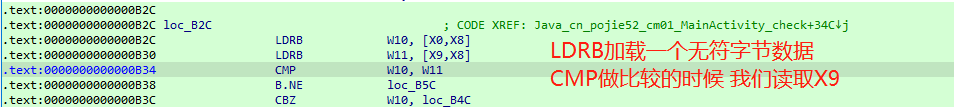
function hook_B30(){
var offset = 0xB30;
var base_model = Process.getModuleByName("libnative-lib.so")
var fun_address = base_model.base.add(offset);
Interceptor.attach(fun_address,{
onEnter:function(args){
console.log("onenter")
console.log(Memory.readCString(this.context.x9))
},
onLeave:function(){}
})
}
[Pixel 2 XL::cn.pojie52.cm01]-> onenter
5Gh2/y6Poq2/WIeLJfmh6yesnK7ndnJeWREFjRx8
5、获取结果
直接进行RC4解密逻辑。
import base64
def encrypt_logic(key, ciphertext):
S = rc4_init(key)
i = j = 0
result = ''
for a in ciphertext:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = chr(ord(a) ^ S[(S[i] + S[j]) % 256])
result += k
return result
def rc4_init(key): # S盒初始化置换,K为密钥
S = []
j = 0
k = [] # 临时数组
for i in range(256):
S.append(i)
k.append(key[i % len(key)])
for i in range(256):
j = (j + S[i] + ord(k[i])) % 256
S[i], S[j] = S[j], S[i] # 交换S[i],S[j]
return S
def rc4_encrypt(key,ciphertext):
result = encrypt_logic(key,ciphertext)
return base64.b64encode(result)
def rc4_decrypt(key,ciphertext):
result = encrypt_logic(key,base64.b64decode(ciphertext))
return result
if __name__ == '__main__':
key = 'areyousure??????'
en_ciphertext = '5Gh2/y6Poq2/WIeLJfmh6yesnK7ndnJeWREFjRx8'
de_ciphertext = rc4_decrypt(key, en_ciphertext)
print("Decrypt:" + de_ciphertext)
Decrypt:52pojieHappyChineseNewYear2021
总结:虽然RC4的特征看起来不是很明显,密钥流的产生过程及异或运算的特征来确定是否是RC4,当然,因为RC4属于流加密,所以也可以把明文的长度和加密后的长度是否相等作为入手点。apk样例来自52破解春节安卓题。